Easy Shape Command Icons Will Cause a Spider Web Image to Show Up on the Monitor
Overview
This guide is intended to serve as a basic introduction for using ZAP to perform security testing, even if you don't accept a background in security testing. To that end, some security testing concepts and terminology is included merely this certificate is not intended to exist a comprehensive guide to either ZAP or security testing.
It is also available as a pdf to make it easier to impress.
Security Testing Basics
Software security testing is the procedure of assessing and testing a system to discover security risks and vulnerabilities of the system and its data. There is no universal terminology only for our purposes, we define assessments every bit the assay and discovery of vulnerabilities without attempting to actually exploit those vulnerabilities. We define testing equally the discovery and attempted exploitation of vulnerabilities.
Security testing is oft broken out, somewhat arbitrarily, according to either the type of vulnerability existence tested or the blazon of testing being done. A common breakout is:
- Vulnerability Assessment – The system is scanned and analyzed for security issues.
- Penetration Testing – The organization undergoes analysis and attack from simulated malicious attackers.
- Runtime Testing – The system undergoes assay and security testing from an end-user.
- Code Review – The organization code undergoes a detailed review and analysis looking specifically for security vulnerabilities.
Note that risk assessment, which is normally listed every bit office of security testing, is not included in this list. That is considering a risk cess is not actually a examination but rather the analysis of the perceived severity of unlike risks (software security, personnel security, hardware security, etc.) and any mitigation steps for those risks.
More About Penetration Testing
Penetration Testing (pentesting) is carried out as if the tester was a malicious external attacker with a goal of breaking into the system and either stealing information or carrying out some sort of denial-of-service attack.
Pentesting has the advantage of beingness more authentic because it has fewer false positives (results that written report a vulnerability that isn't actually present), merely tin can exist time-consuming to run.
Pentesting is also used to test defense force mechanisms, verify response plans, and confirm security policy adherence.
Automated pentesting is an important part of continuous integration validation. It helps to uncover new vulnerabilities also as regressions for previous vulnerabilities in an environs which quickly changes, and for which the development may be highly collaborative and distributed.
The Pentesting Process
Both transmission and automated pentesting are used, oft in conjunction, to test everything from servers, to networks, to devices, to endpoints. This document focuses on web application or spider web site pentesting.
Pentesting usually follows these stages:
- Explore – The tester attempts to learn well-nigh the organisation being tested. This includes trying to make up one's mind what software is in utilize, what endpoints exist, what patches are installed, etc. It too includes searching the site for hidden content, known vulnerabilities, and other indications of weakness.
- Assault – The tester attempts to exploit the known or suspected vulnerabilities to prove they exist.
- Report – The tester reports back the results of their testing, including the vulnerabilities, how they exploited them and how hard the exploits were, and the severity of the exploitation.
Pentesting Goals
The ultimate goal of pentesting is to search for vulnerabilities so that these vulnerabilities can exist addressed. Information technology can also verify that a organisation is not vulnerable to a known class or specific defect; or, in the case of vulnerabilities that have been reported as fixed, verify that the system is no longer vulnerable to that defect.
Introducing ZAP
Zed Set on Proxy (ZAP) is a free, open-source penetration testing tool being maintained nether the umbrella of the Open up Web Application Security Project (OWASP). ZAP is designed specifically for testing web applications and is both flexible and extensible.
At its core, ZAP is what is known as a "human being-in-the-middle proxy." It stands between the tester's browser and the spider web application so that it tin can intercept and inspect letters sent between browser and web awarding, modify the contents if needed, then forrard those packets on to the destination. It tin exist used as a stand-lonely awarding, and as a daemon process.

If there is another network proxy already in utilize, equally in many corporate environments, ZAP can exist configured to connect to that proxy.

ZAP provides functionality for a range of skill levels – from developers, to testers new to security testing, to security testing specialists. ZAP has versions for each major Bone and Docker, so you are not tied to a single OS. Additional functionality is freely available from a diversity of add-ons in the ZAP Marketplace, accessible from within the ZAP client.
Considering ZAP is open up-source, the source lawmaking can be examined to run into exactly how the functionality is implemented. Anyone can volunteer to work on ZAP, prepare bugs, add together features, create pull requests to pull fixes into the project, and writer add-ons to support specialized situations.
Every bit with most open up source projects, donations are welcome to help with costs for the projects. You tin find a donate button on the owasp.org page for ZAP at https://owasp.org/world wide web-projection-zap/.
Install and Configure ZAP
ZAP has installers for Windows, Linux, and Mac Bone/Ten. In that location are also Docker images available on the download site listed below.
Install ZAP
The first thing to exercise is install ZAP on the organisation you intend to perform pentesting on. Download the advisable installer from the Download page.
Note that ZAP requires Coffee 8+ in guild to run. The Mac Bone/Ten installer includes an appropriate version of Coffee but you must install Java eight+ separately for Windows, Linux, and Cross-Platform versions. The Docker versions practice not crave you to install Java.
One time the installation is complete, launch ZAP and read the license terms. Click Agree if you lot accept the terms, and ZAP will cease installing, and then ZAP will automatically start.
Persisting a Session
When you lot outset start ZAP, you will be asked if you want to persist the ZAP session. By default, ZAP sessions are always recorded to disk in a HSQLDB database with a default proper name and location. If you do not persist the session, those files are deleted when you lot exit ZAP.
If you choose to persist a session, the session information will exist saved in the local database so yous can admission it later, and y'all volition be able to provide custom names and locations for saving the files.
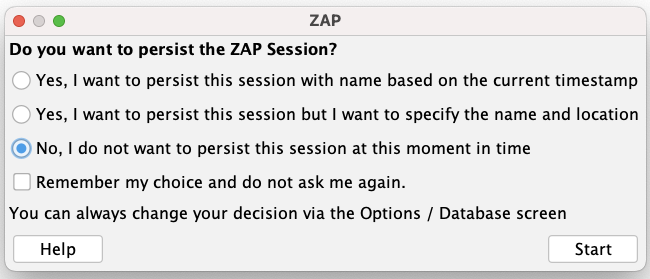
For now, select No, I do not want to persist this session at this moment in time, and then click Start. The ZAP sessions will not be persisted for now.
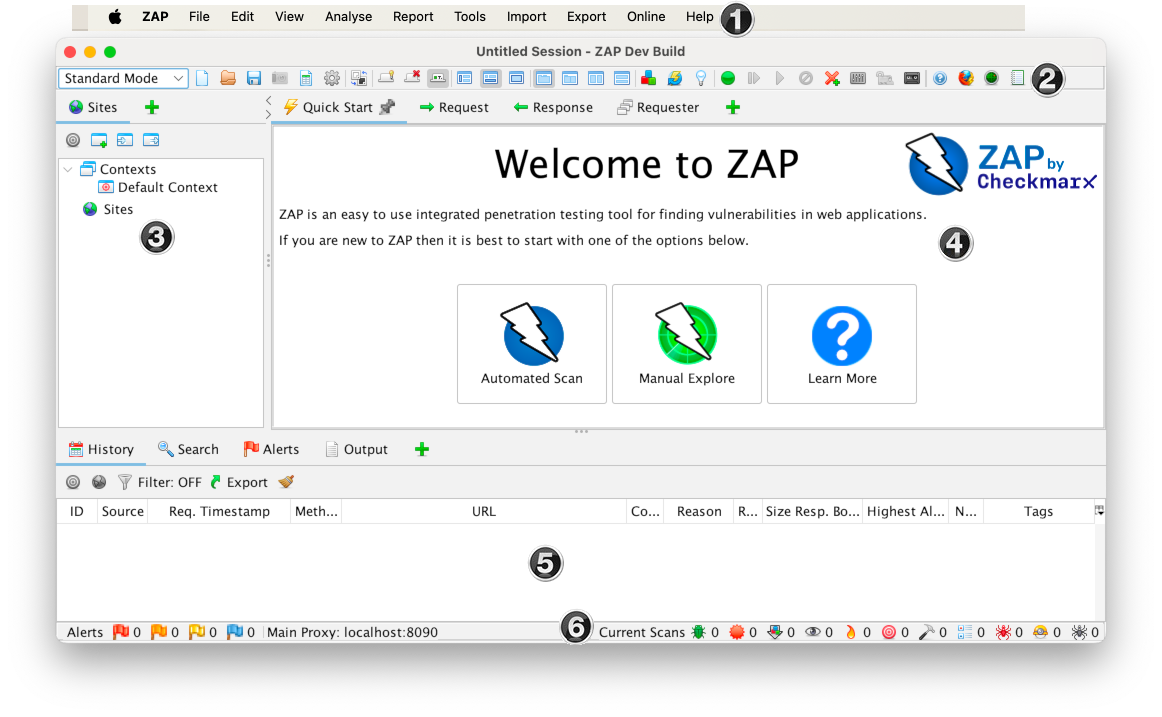
ZAP Desktop UI
The ZAP Desktop UI is composed of the following elements:
- Menu Bar – Provides access to many of the automated and manual tools.
- Toolbar – Includes buttons which provide easy access to about commonly used features.
- Tree Window – Displays the Sites tree and the Scripts tree.
- Workspace Window – Displays requests, responses, and scripts and allows you to edit them.
- Information Window – Displays details of the automatic and transmission tools.
- Footer – Displays a summary of the alerts found and the status of the main automated tools.
While using ZAP, yous tin click Aid on the Card Bar or printing F1 to admission context-sensitive aid from the ZAP Desktop User Guide. It is also available online.
For more data virtually the UI, see ZAP UI Overview in the ZAP online documentation.
ZAP likewise supports a powerful API and command line functionality, both of which are beyond the scope of this guide.
Important: You should only apply ZAP to attack an awarding you accept permission to exam with an active assail. Because this is a simulation that acts similar a real attack, actual damage can exist washed to a site'due south functionality, information, etc. If you are worried about using ZAP, you can prevent it from causing harm (though ZAP's functionality will exist significantly reduced) by switching to rubber style.
To switch ZAP to safe mode, click the arrow on the fashion dropdown on the main toolbar to aggrandize the dropdown list and select Safe Mode.
Running an Automated Scan
The easiest way to start using ZAP is via the Quick Start tab. Quick Showtime is a ZAP improver that is included automatically when y'all installed ZAP.
To run a Quick Start Automated Scan :
- First ZAP and click the Quick Start tab of the Workspace Window.
- Click the large Automated Scan button.
- In the URL to attack text box, enter the total URL of the web application you want to assail.
- Click the Attack
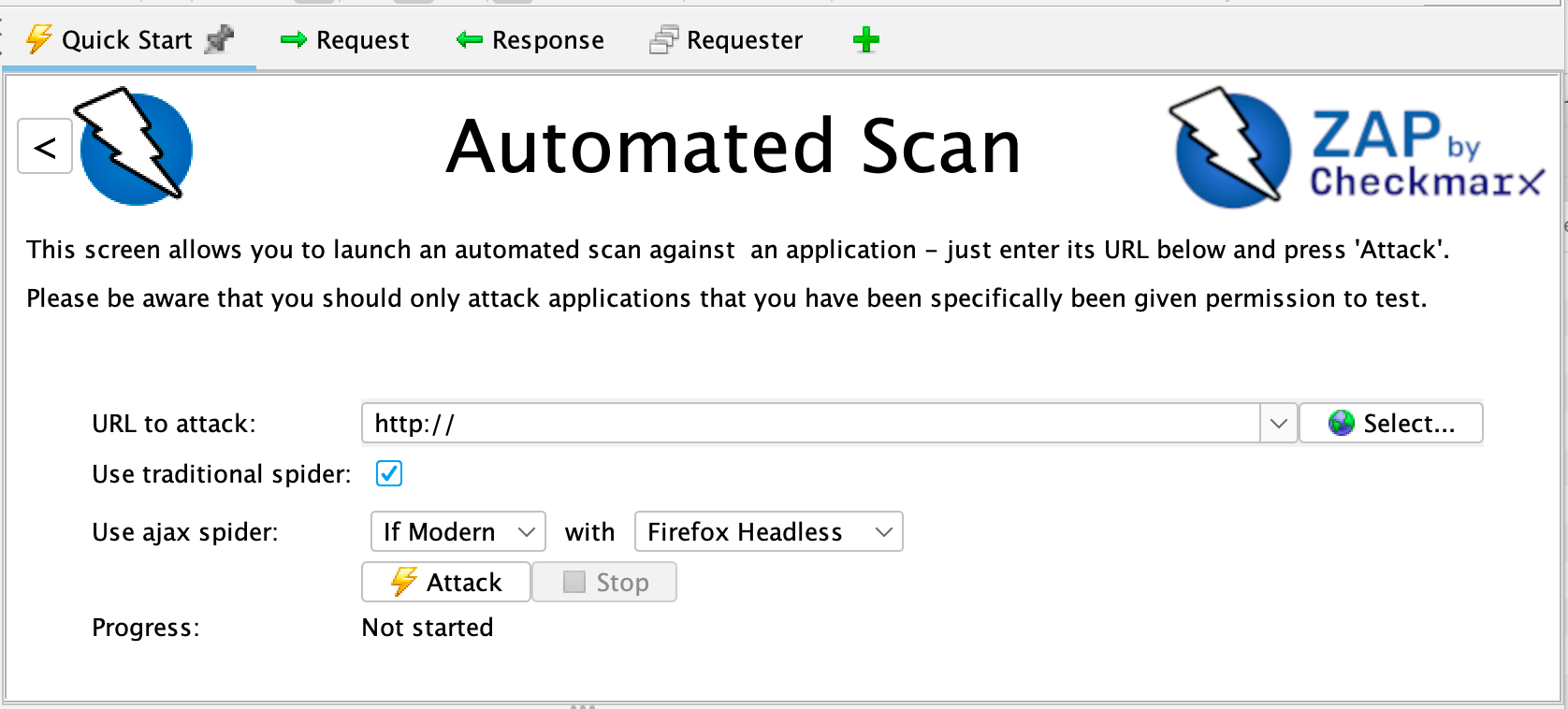
ZAP will go along to crawl the web application with its spider and passively scan each page it finds. Then ZAP will utilise the agile scanner to attack all of the discovered pages, functionality, and parameters.
ZAP provides 2 spiders for crawling web applications, yous can apply either or both of them from this screen.
The traditional ZAP spider which discovers links by examining the HTML in responses from the spider web application. This spider is fast, only it is not always effective when exploring an AJAX web awarding that generates links using JavaScript.
For AJAX applications, ZAP's AJAX spider is likely to be more effective. This spider explores the web application past invoking browsers which then follow the links that have been generated. The AJAX spider is slower than the traditional spider and requires additional configuration for utilize in a "headless" environment.
ZAP will passively scan all of the requests and responses proxied through it. And then far ZAP has only carried out passive scans of your web application. Passive scanning does not alter responses in whatsoever way and is considered safety. Scanning is also performed in a background thread to not slow downwardly exploration. Passive scanning is good at finding some vulnerabilities and as a way to get a feel for the basic security state of a web awarding and locate where more investigation may be warranted.
Active scanning, still, attempts to observe other vulnerabilities by using known attacks against the selected targets. Active scanning is a existent assail on those targets and can put the targets at hazard, so do not use active scanning against targets you do non have permission to test.
Translate Your Test Results
As ZAP spiders your web awarding, information technology constructs a map of your web applications' pages and the resources used to return those pages. Then it records the requests and responses sent to each page and creates alerts if at that place is something potentially incorrect with a request or response.
See Explored Pages
To examine a tree view of the explored pages, click the Sites tab in the Tree Window. You tin can aggrandize the nodes to come across the individual URLs accessed.
View Alerts and Alarm Details
The left-paw side of the Footer contains a count of the Alerts found during your test, cleaved out into risk categories. These take chances categories are:
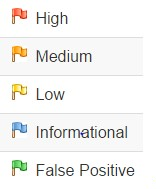
To view the alerts created during your test:
- Click the Alerts tab in the Data Window.
- Click each alert displayed in that window to display the URL and the vulnerability detected in the correct side of the Data Window.
- In the Workspace Windows, click the Response tab to run across the contents of the header and torso of the response. The part of the response that generated the alert will exist highlighted.
Exploring an Application Manually
The passive scanning and automated attack functionality is a dandy fashion to brainstorm a vulnerability assessment of your web application simply it has some limitations. Amongst these are:
- Any pages protected by a login page are not discoverable during a passive scan because, unless yous've configured ZAP's authentication functionality, ZAP will not handle the required authentication.
- You don't have a lot of command over the sequence of exploration in a passive scan or the types of attacks carried out in an automated attack. ZAP does provide many additional options for exploration and attacks outside of passive scanning.
Spiders are a smashing way to explore your basic site, but they should be combined with manual exploration to exist more constructive. Spiders, for example, will only enter basic default data into forms in your web application but a user can enter more than relevant information which can, in plough, expose more than of the web application to ZAP. This is especially truthful with things like registration forms where a valid email accost is required. The spider may enter a random string, which will cause an error. A user will be able to react to that error and supply a correctly formatted string, which may cause more of the awarding to exist exposed when the course is submitted and accustomed.
You should explore all of your web application with a browser proxying through ZAP. As you do this, ZAP passively scans all the requests and responses made during your exploration for vulnerabilities, continues to build the site tree, and records alerts for potential vulnerabilities found during the exploration.
Information technology is important to take ZAP explore each folio of your spider web application, whether linked to another page or not, for vulnerabilities. Obscurity is not security, and hidden pages sometimes go live without alarm or notice. So be as thorough every bit you tin when exploring your site.
Yous can quickly and hands launch browsers that are pre-configured to proxy through ZAP via the Quick Kickoff tab. Browsers launched in this fashion will also ignore any document validation warnings that would otherwise be reported.
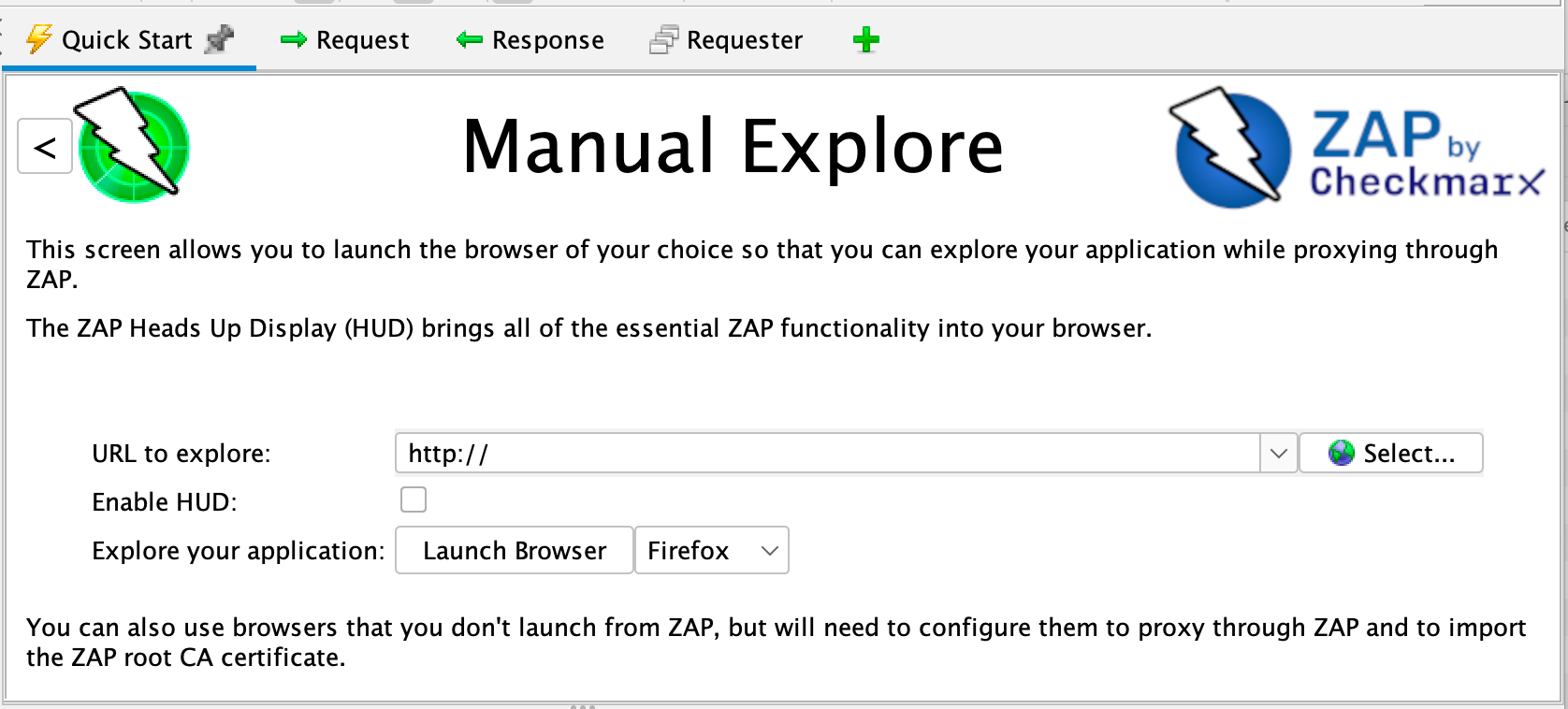
To Manually Explore your application:
- Start ZAP and click the Quick First tab of the Workspace Window.
- Click the big Manual Explore push button.
- In the URL to explore text box, enter the full URL of the web awarding you want to explore.
- Select the browser you would like to use
- Click the Launch Browser
This option will launch whatsoever of the most mutual browsers that you take installed with new profiles.
If you would similar to use any of your browsers with an existing profile, for example with other browser add-ons installed, then you lot will demand to manually configure your browser to proxy via ZAP and import and trust the ZAP Root CA Certificate. Run into the ZAP Desktop User Guide for more than details.
By default the ZAP Heads Upward Display (HUD) volition be enabled. Unchecking the relevant option on this screen earlier launching a browser will disable the HUD.
The Heads Up Brandish
The Heads Up Display (HUD) is a new an innovative interface that provides access to ZAP functionality directly in the browser. It is ideal for people new to web security and too allows experienced penetration testers to focus on an applications functionality while providing key security data and functionality.

The HUD is overlayed on top of the target application in your browser when enabled via the 'Manual Explore' screen or toolbar option. Only modern browsers such every bit Firefox and Chrome are supported.
By default a splash screen is shown for the HUD which includes a link to a tutorial which volition take you through the HUD features and explain how you can utilize them.
ZAP Avant-garde Features
Advanced Desktop Features
The desktop has a large number of features that are not immediately apparent and so that new users are not overwhelmed.
There are many tabs that are not shown by default. They can be accessed via the right hand tabs with light-green '+' icons. You tin can pin any tabs you would like to always appear by right clicking on them. Many of the tabs hidden past default will appear when relevant. For example the Websockets tab will appear if an awarding you are proxying through ZAP starts to utilize Websockets.
The desktop also makes heavy use of context sensitive right click options, so right click everywhere while you are getting used to the user interface.
The ZAP Marketplace
The ZAP desktop has a plugin compages which means that new functionality tin can be added dynamically.
An online marketplace provides a wide range of ZAP add together-ons which add many boosted features to ZAP.
The marketplace tin be accessed from within ZAP via the 'Manage Add-ons' button on the toolbar:
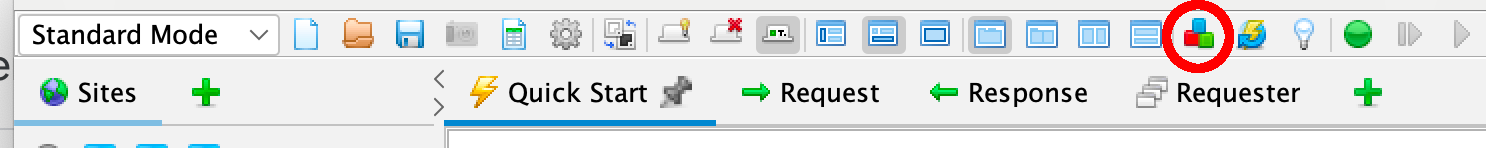
All of the add-ons on the marketplace are completely free.
Automation
ZAP is an ideal tool to utilize in automation and supports a range of options:
- Docker Packaged Scans
- GitHub Actions
- Automation Framework
- API and Daemon way
Larn More About ZAP
Now that you are familiar with a few basic capabilities of ZAP, you can larn more nigh ZAP's capabilities and how to use them from ZAP'southward Desktop User Guide. The User Guide provides step-by-step instructions, references for the API and control-line programming, instructional videos, and tips and tricks for using ZAP.
Boosted links are also available via the 'Learn More' button on the Quick Start top screen:
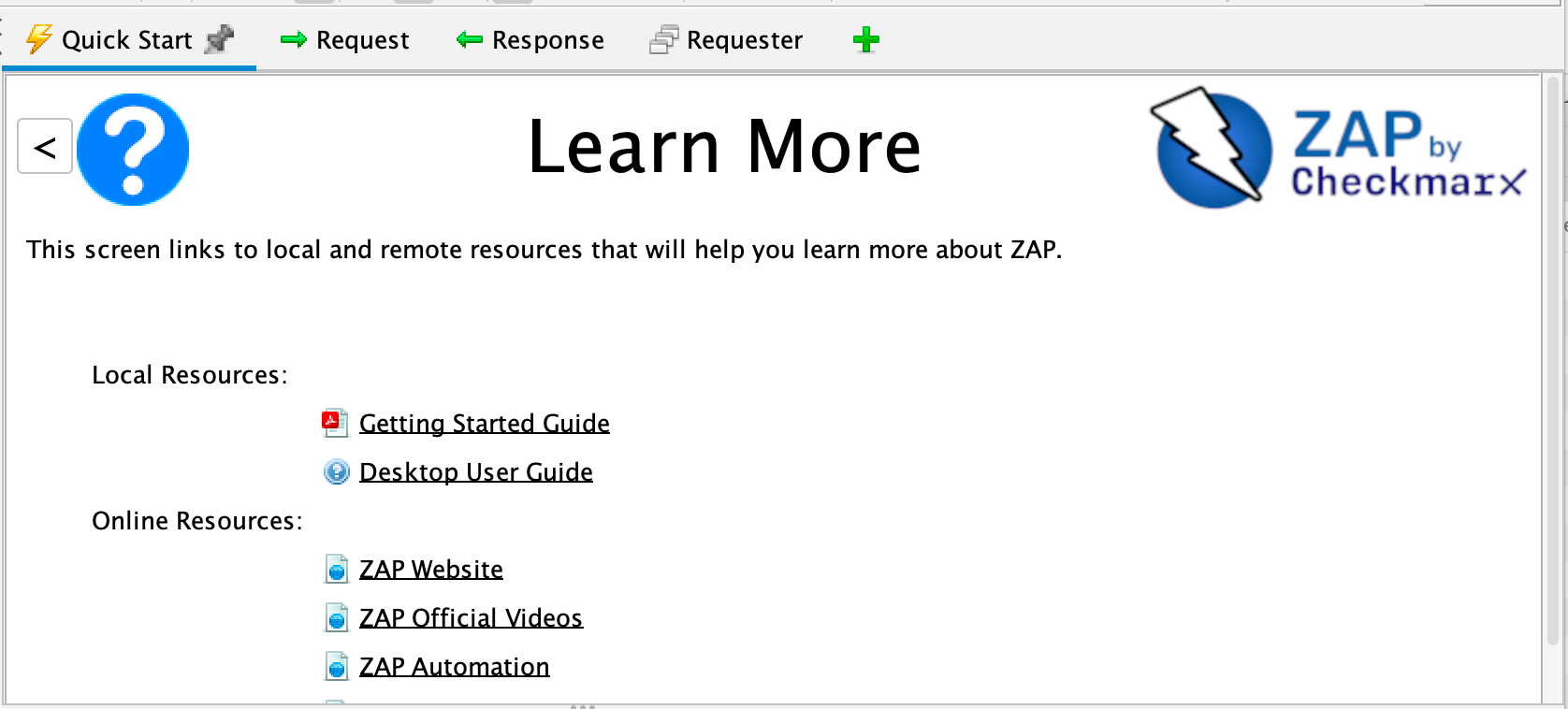
The screen links to both local resource (if available) and online content.
fergusontheessale.blogspot.com
Source: https://www.zaproxy.org/getting-started/
0 Response to "Easy Shape Command Icons Will Cause a Spider Web Image to Show Up on the Monitor"
Post a Comment